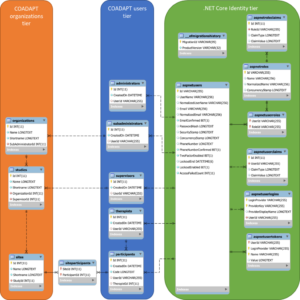
The COADAPT platform allows managing the organizations and the people involved in ageing workforce studies via its entities and data management functionalities. It also manages participants’ data via its participant information management functionalities. As such, the platform facilitates building COADAPT applications, which either send data to the platform or receive data from it. In the core of the COADAPT platform lies the data model split into two: The entities management data model describes the different people entities involved in the studies, making sure that there is an organizational hierarchy with the correct data access rights. The entities are split into three tiers, as shown below:
- The COADAPT organizations tier contains the entities hosting the studies.
- The COADAPT users tier contains the entities of the different user types.
- The .NET Core Identity tier is managed by Identity to provide authentication and authorization.
The participant information data model manages data measured from devices or reported from healthcare professionals. All the COADAPT components communicate with each other via the platform, utilizing two exposed REST APIs.
Platform architecture
The COADAPT platform is deployed in 3 containers (logical servers): .NET Core back-end, Angular front-end, and MySQL database.
All three containers are included in a pod (group of containers). Note that although currently one such pod is deployed (still in the development phase), during the normal operation (production phase) there will be as many pods as there are trial sites.
Kubernetes is used to manage pod deployment on nodes. Kubernetes is a portable, extensible, open-source platform for managing containerized workloads and services. It deploys pods in nodes, the actual machine partitions provided for the pods. The current pod is deployed on a node with 2 vCPUs and 2GB RAM. Kubernetes can easily manage any upgrades needed when in the production phase.
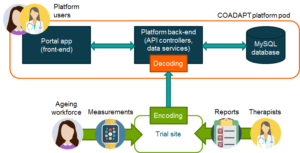
Platform data security
An important chapter is the data security of the platform. For that reason, the platform features roles-based access, enforcing strict data access constraints. Platform users need to log in with an email/password to obtain JWT to authorize access to every API endpoint.
Then the data is sent to the platform from the trial sites in encrypted form by using private/public key pairs. Data is pseudo-anonymized, as the platform only stores participants’ codes. This ensures that the names of the participants are nowhere on the platform.
The platform is deployed in HIPAA compliant infrastructure. Physical and network security is guaranteed since the production version will be on Azure, the database will be encrypted and there is role-based access. Process security is also guaranteed since the platform developer, Innovation Sprint is certified with ISO27001.